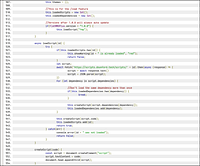
FlatChat+ беше докладван 21.01.2026 за Неразрешен външен код
Докладващият каза:
It appears to be loading arbitrary scripts from https://scripts.dounford.tech/ on line 526. I attached a screenshot of the relevant code
Felipe Dounford каза:
This is indeed a feature, it has a command /load where you can load other scripts from the game, you can check the list with /scripts I'm a moderator in the game and also have a chat bot that handles the backend code of the /load This piece of code is only run on login if the person already loaded the script before with /load, when the person uses /load or if the person is using a very old version of the fmp dependency it would auto update it (some users were having problems updating it because dependencies are not auto updated by default on tampermonkey) This feature is well know in the community and I talk about it in almost every update of other scripts saying something like "Also available on FlatChat with /load"
Докато изпращахте доклада, същевременно скриптът беше обновен.
Този скрипт е имал 1 предишен задържан или оправен доклад.
Felipe Dounford (докладваният потребите) направи:
Този доклад е одобрен от модератор.
One of the core principles of Greasy Fork is that the user must be able to inspect the code in a script. External scripts can bypass this principle in a number of ways: they can change without warning or history, they can serve up different code to different people, and they can be used to hide malicious code in the middle of known libraries. Even if someone were to check an external script and determine it to be legitimate, that would be no guarantee that that script always has been or always will be legitimate. More info on external scripts: https://greasyfork.org/help/external-scripts